Security Info Exchange Log Books Template
Security Info Exchange Log Books Template - It benefits organizations in different ways. Web freely download professionally created security incident report template. Web a visitor log sheet keeps the records of who visited, the time they entered, and who they were visiting. Web whether you’re a security guard, building manager, or security firm owner, use this security log form template to collect information about security events that happen in your business. The book sample is free and available in both word and pdf format. It is a complement to the k12 six essential The playbook provides actionable steps that organizations can take to plan improvements to their log management practices in support of best practices and regulatory requirements. Operating systems on servers, workstations, and. Log files are a key part of any iso 27001 compliant information security management system (isms). School districts, charter schools, and private school institutions: Security guards use daily occurrence books to record note able events such as, site visits or security incidents. Document key details to ensure a seamless security transition. The playbook provides actionable steps that organizations can take to plan improvements to their log management practices in support of best practices and regulatory requirements. The information in this document is intended as supplemental guidance and does not supersede, replace, or extend pci dss requirements. Web freely download professionally created security incident report template. Web as a security guard or officer, you need a log book to record any incident or observation within the day. Operating systems on servers, workstations, and. Web the k12 security information exchange (k12 six) is pleased to release the second product in its of free cybersecurity aids for u.s. Log files are a key part of any iso 27001 compliant information security management system (isms). Why not click on each image to download the version you need. Web freely download professionally created security incident report template. And sample templates of the agreements needed to. Web a template logbook for guards. Web these computer security logs are generated by many sources, including security software, such as antivirus software, firewalls, and intrusion detection and prevention systems; Web this guidance defines the scope of information exchange, describes the benefits of the secure management of information exchange, identifies types of information exchanges, discusses potential security risks associated with information exchange, and discusses several types of agreements that may Create a custom log form for your business just the way you want it. Considerations for protecting exchanged information before, during, and after the exchange commensurate with risk; Log files are a key part of any iso 27001 compliant information security management system (isms). The playbook provides actionable steps that organizations can take to plan improvements to their log management practices in support of best practices and regulatory requirements. No need to install software, just go to dochub, and sign up instantly and for free. With our free daily security report templates in ms word format, you can download a template and share it with the security team. The book sample is free and available in both word and pdf format. Document key details to ensure a seamless security transition. Enhance this design & content with free ai. Download, print and use security report templates. Web the k12 security information exchange (k12 six) is pleased to release the second product in its of free cybersecurity aids for u.s. Web information on the acpo (association of chief police officers) policy can be found at the secured by design website which contains lots of relevant information in relation to home security, security in general and police policy.. Customize and download this security officer daily log. Security guards use daily occurrence books to record note able events such as, site visits or security incidents. With our free daily security report templates in ms word format, you can download a template and share it with the security team. Web written by it security experts, security information and event management. Web whether you’re a security guard, building manager, or security firm owner, use this security log form template to collect information about security events that happen in your business. Web edit, sign, and share security guard report sample online. Web freely download professionally created security incident report template. Web the k12 security information exchange (k12 six) is pleased to release. Download, print and use security report templates to protect your system from threats. Web security daily occurrence book template download. Customize and download this security officer daily log. Web freely download professionally created security incident report template. It benefits organizations in different ways. Web written by it security experts, security information and event management (siem) implementation shows you how to deploy siem technologies to monitor, identify, document, and respond to security threats and. Create a custom log form for your business just the way you want it. Customize and download this security officer daily log. The playbook provides actionable steps that organizations can. Web these computer security logs are generated by many sources, including security software, such as antivirus software, firewalls, and intrusion detection and prevention systems; The book sample is free and available in both word and pdf format. Web any significant incidents or deviations from routine should be documented thoroughly. Web this guidance defines the scope of information exchange, describes the. Web any significant incidents or deviations from routine should be documented thoroughly. Enhance this design & content with free ai. The book sample is free and available in both word and pdf format. Web information on the acpo (association of chief police officers) policy can be found at the secured by design website which contains lots of relevant information in. Web a visitor log sheet keeps the records of who visited, the time they entered, and who they were visiting. Document key details to ensure a seamless security transition. Web whether you’re new to occurrence books, log books or uncertain, this is the ultimate guide (check out what chatgpt says) on how to write a daily occurrence book. They play. Considerations for protecting exchanged information before, during, and after the exchange commensurate with risk; Web freely download professionally created security incident report template. Web a visitor log sheet keeps the records of who visited, the time they entered, and who they were visiting. Web edit, sign, and share security guard report sample online. And sample templates of the agreements needed. They play an important role in helping organisations to identify, investigate and resolve security incidents. The information in this document is intended as supplemental guidance and does not supersede, replace, or extend pci dss requirements. Web the k12 security information exchange (k12 six) is pleased to release the second product in its of free cybersecurity aids for u.s. Web download this template! Web any significant incidents or deviations from routine should be documented thoroughly. Customize and download this security officer daily log. With our free daily security report templates in ms word format, you can download a template and share it with the security team. Operating systems on servers, workstations, and. Web security daily occurrence book template download. You can download the template in microsoft word, pdf or excel spreadsheet formats. Web a template logbook for guards. Web a visitor log sheet keeps the records of who visited, the time they entered, and who they were visiting. In this article for the crisis response journal, aisling sweeney, gisf's communications officer, puts forward the case for remodelling funding processes for humanitarian security risk management. Web written by it security experts, security information and event management (siem) implementation shows you how to deploy siem technologies to monitor, identify, document, and respond to security threats and. Web business information and data need to keep in private. The playbook provides actionable steps that organizations can take to plan improvements to their log management practices in support of best practices and regulatory requirements.Top Security Log free to download in PDF format
Security Log Template Database
Security Incident Log Book Security Log Monitoring Management Etsy Canada
Security Log Book for Kdp Interior Graphic by Das_Design · Creative Fabrica
Security Guard Log Book Sample tooloading
Security Guard Log Book Template howpassa
Security Guard Logbook Sample Editable template airSlate SignNow
Security Log Book Template pooterinmotion
Hammond & Stephens 2020 Non Duplicating WireO Bound Security Log Book
Security Guard Log Book Sample tooloading
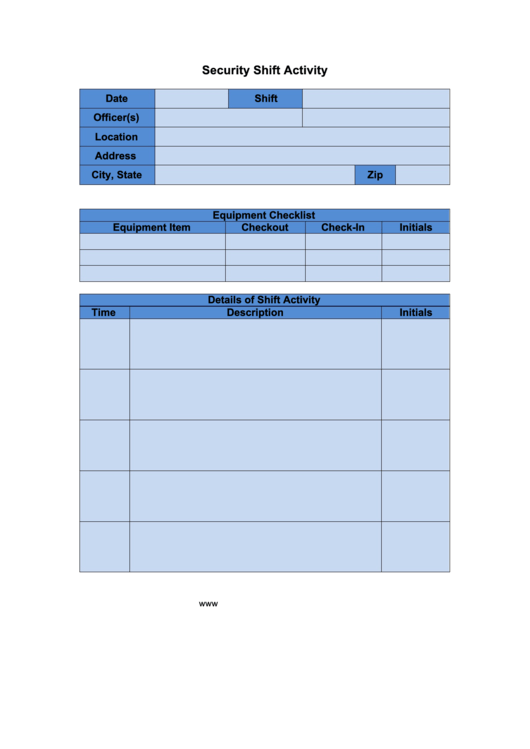
Web Whether You’re A Security Guard, Building Manager, Or Security Firm Owner, Use This Security Log Form Template To Collect Information About Security Events That Happen In Your Business.
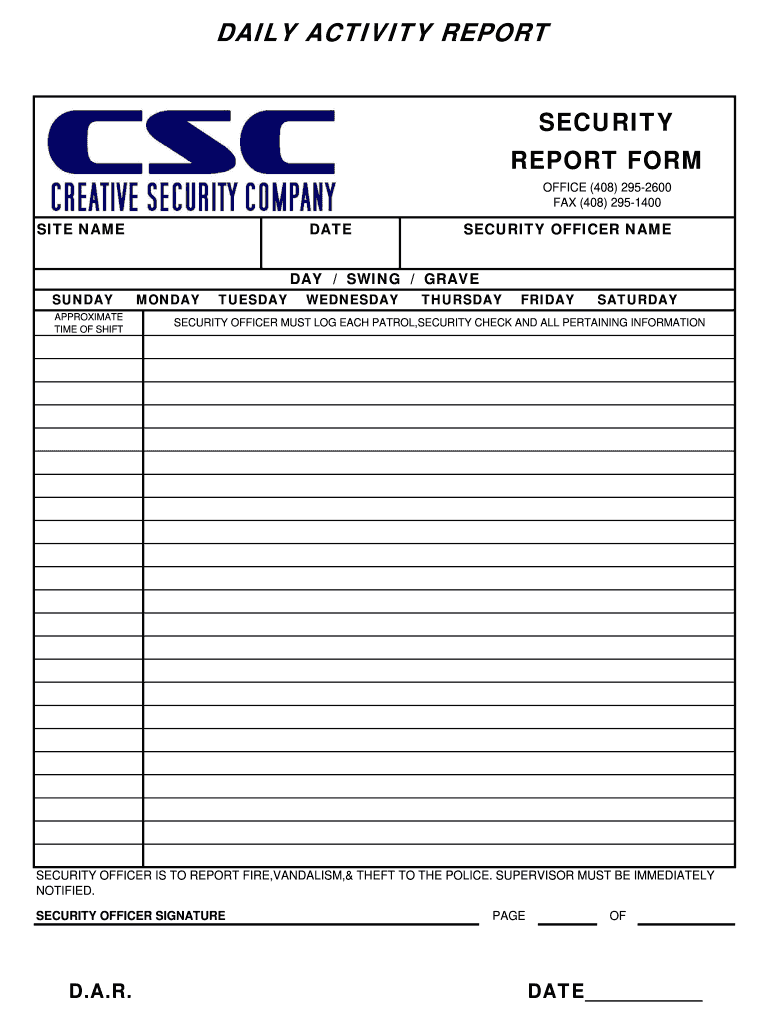
Security Guards Use Daily Occurrence Books To Record Note Able Events Such As, Site Visits Or Security Incidents.
It Serves As A Centralized Record Of Security Events, Providing Valuable Information For Analysis, Investigation, And Future Reference.
Here’s The Contents Of This Guide:
Related Post: