System Security Plan Template
System Security Plan Template - Web a system security plan (ssp) defines the boundary of connected components that make up an information system and outlines how you implement security requirements. The protection of a system must be documented in a system security plan. 1 system security requirements and describes controls in place or planned to meet those requirements. Web this system security plan (ssp) template provides a guide and resource to assist organisations in preparing a ssp describing organisational policies and processes relating to, and technical controls implemented within, system (s). The protection of a system must be documented in a system security plan. The protection of a system must be documented in a system security plan. Web the dod's number one cybersecurity requirement is to have a system security plan. Learn how to create a system security plan for your organization. Web the new cmmc guidelines include requirements to develop, document, and maintain ssps that describe system boundaries and operating environments a system security plan and plans of action that all cmmc 2.0 levels. Web the system security plan describes the controls in place, or planned for implementation, to provide a level of security appropriate for the information to be transmitted, processed, or stored by a system. Web planning note (04/13/2022): The protection of a system must be documented in a system security plan. Web july 23 | 2020. Web nist computer security resource center Web the new cmmc guidelines include requirements to develop, document, and maintain ssps that describe system boundaries and operating environments a system security plan and plans of action that all cmmc 2.0 levels. Web the objective of system security planning is to improve protection of information system resources. Web the dod's number one cybersecurity requirement is to have a system security plan. All federal systems have some level of sensitivity and require protection as part of good management practice. 1 system security requirements and describes controls in place or planned to meet those requirements. This is a “living document” that is meant to be updated as conditions change. Web there is now one template each for the ssp, sap and sar. Web the oscal ssp model enables full modeling of highly granular ssp content, including points of contact, system characteristics, and control satisfaction descriptions. Web the new cmmc guidelines include requirements to develop, document, and maintain ssps that describe system boundaries and operating environments a system security plan and plans of action that all cmmc 2.0 levels. Web a system security plan (ssp) defines the boundary of connected components that make up an information system and outlines how you implement security requirements. All federal systems have some level of sensitivity and require protection as part of good management practice. All federal systems have some level of sensitivity and require protection as part of good management practice. Web develop, document, and periodically update system security plans that describe system boundaries, system environments of operation, how security requirements are implemented, and the relationships with or connections to other systems. Web the dod's number one cybersecurity requirement is to have a system security plan. Some companies have their internal it staff fill in this template to create a system security plan. All federal systems have some level of sensitivity and require protection as part of good management practice. The protection of a system must be documented in a system security plan. Art clomera, vice president operations. Web the oscal ssp model enables full modeling of highly granular ssp content, including points of contact, system characteristics, and control satisfaction descriptions. Web the objective of system security planning is to improve protection of information technology (it) resources. This approach can. Fedramp released updates to the system security plan (ssp) attachment 12 template, the fedramp master acronym and glossary document, and the fedramp initial authorization package checklist template. 1 system security requirements and describes controls in place or planned to meet those requirements. Web the dod's number one cybersecurity requirement is to have a system security plan. Web july 23 |. The protection of a system must be documented in a system security plan. All federal systems have some level of sensitivity and require protection as part of good management practice. Web the objective of system security planning is to improve protection of information system resources. The protection of a system must be documented in a system security plan. Web the. All federal systems have some level of sensitivity and require protection as part of good management practice. Web the objective of the system security plan (ssp) document is to have a simple, easy‐to‐reference document that covers pertinent information about the controlled unclassified information (cui) environment. This approach can work well if you are sure that your it employees have the. This sar template is used to document assessment results associated with initial assessments, annual assessments, and significant. All federal systems have some level of sensitivity and require protection as part of good management practice. Web july 23 | 2020. Web there is now one template each for the ssp, sap and sar. This is a “living document” that is meant. There are no longer separate sap/sar templates for initial and annual assessments; Stateramp™ is a 501 (c) (6) nonprofit membership organization. Web how to build your system security plan (ssp) with examples and template. Web the system security plan describes the controls in place, or planned for implementation, to provide a level of security appropriate for the information to be. All federal systems have some level of sensitivity and require protection as part of good management practice. Some companies have their internal it staff fill in this template to create a system security plan. Web the objective of system security planning is to improve protection of information technology (it) resources. Web the objective of the system security plan (ssp) document. Web the system security plan describes the controls in place, or planned for implementation, to provide a level of security appropriate for the information to be transmitted, processed, or stored by a system. Learn how to create a system security plan for your organization. Web the objective of system security planning is to improve protection of information technology (it) resources.. Web the objective of system security planning is to improve protection of information technology (it) resources. Web the objective of system security planning is to improve protection of information system resources. Web the objective of the system security plan (ssp) document is to have a simple, easy‐to‐reference document that covers pertinent information about the controlled unclassified information (cui) environment. Web. Stateramp™ is a 501 (c) (6) nonprofit membership organization. Web this system security plan (ssp) template provides a guide and resource to assist organisations in preparing a ssp describing organisational policies and processes relating to, and technical controls implemented within, system (s). There are no longer separate sap/sar templates for initial and annual assessments; Web how to build your system. This is a “living document” that is meant to be updated as conditions change. Web july 23 | 2020. Fedramp released updates to the system security plan (ssp) attachment 12 template, the fedramp master acronym and glossary document, and the fedramp initial authorization package checklist template. Web the objective of system security planning is to improve protection of information system resources. This sar template is used to document assessment results associated with initial assessments, annual assessments, and significant. The protection of a system must be documented in a system security plan. Web the objective of the system security plan (ssp) document is to have a simple, easy‐to‐reference document that covers pertinent information about the controlled unclassified information (cui) environment. Some companies have their internal it staff fill in this template to create a system security plan. Web the system security plan describes the controls in place, or planned for implementation, to provide a level of security appropriate for the information to be transmitted, processed, or stored by a system. Web how to build your system security plan (ssp) with examples and template. Web nist supplies a template to help contractors create an ssp. Learn how to create a system security plan for your organization. The protection of a system must be documented in a system security plan. At a more detailed level, this includes the system's authorization boundary, information types and categorization, inventory, and attachments. All federal systems have some level of sensitivity and require protection as part of good management practice. The same ssp template will be used for the “front matter” sections, with the appropriate control baseline added as an appendix.MustHave System Security Plan Templates with Examples and Samples
Cmmc System Security Plan Template
System Security Plan Ssp Template Workbook Nist Based A Doc
System Security Plan Ssp Template
Fedramp System Security Plan Template
FREE 15+ Sample Security Plan Templates in PDF MS Word Google Docs
Security Management Plan Template
How To Change Your Direct Deposit For Social Security Check Security
Security Plan Templates Documents, Design, Free, Download
FREE 8+ Sample Security Plan Templates in PDF MS Word Google Docs
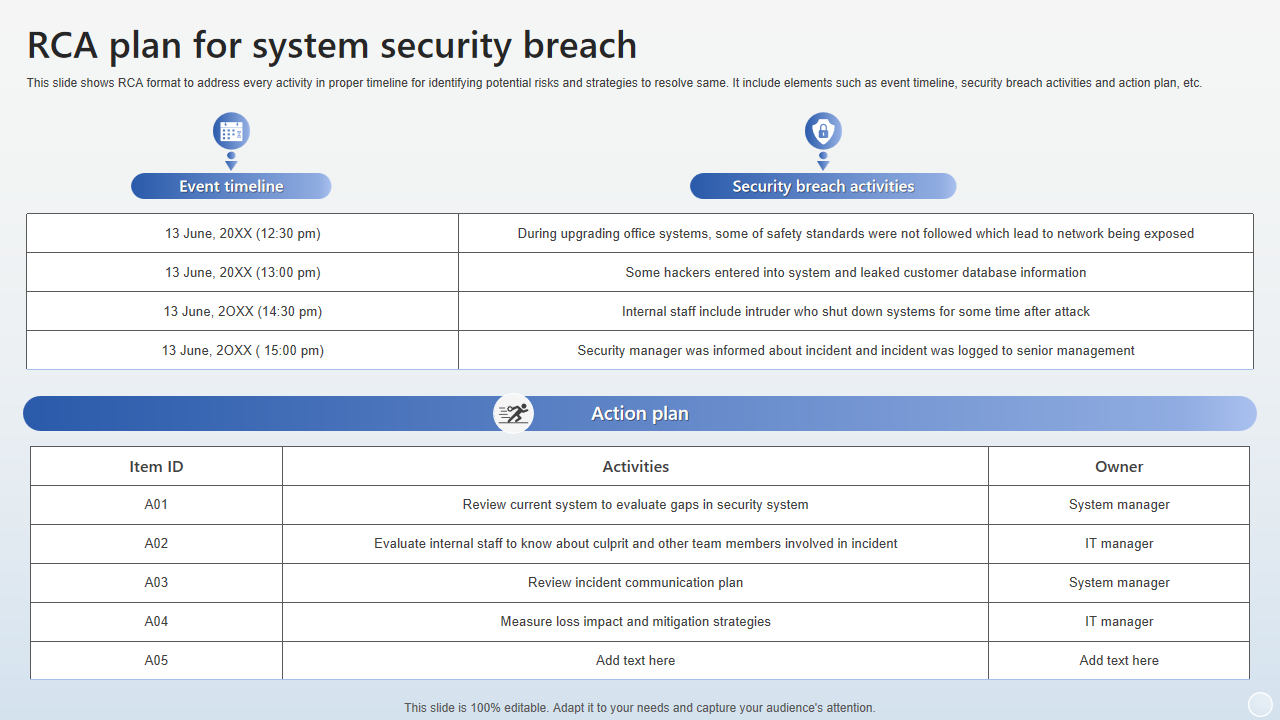
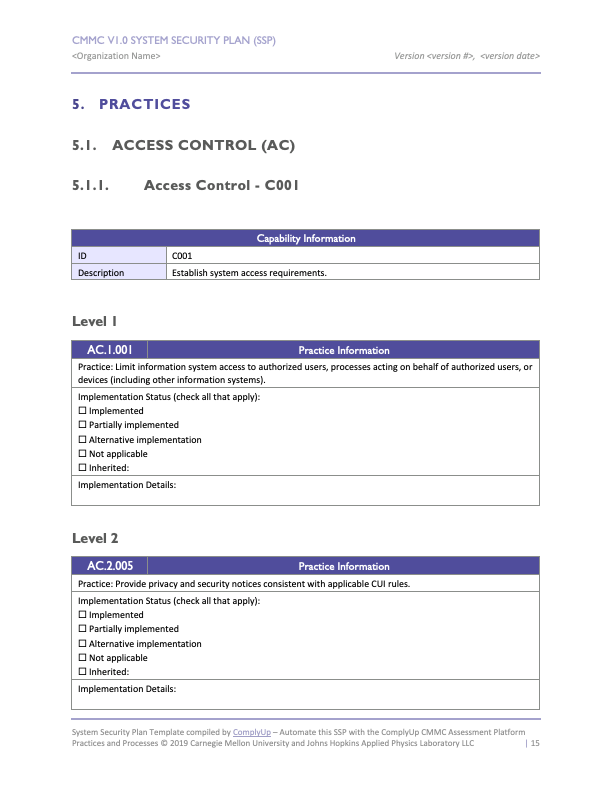
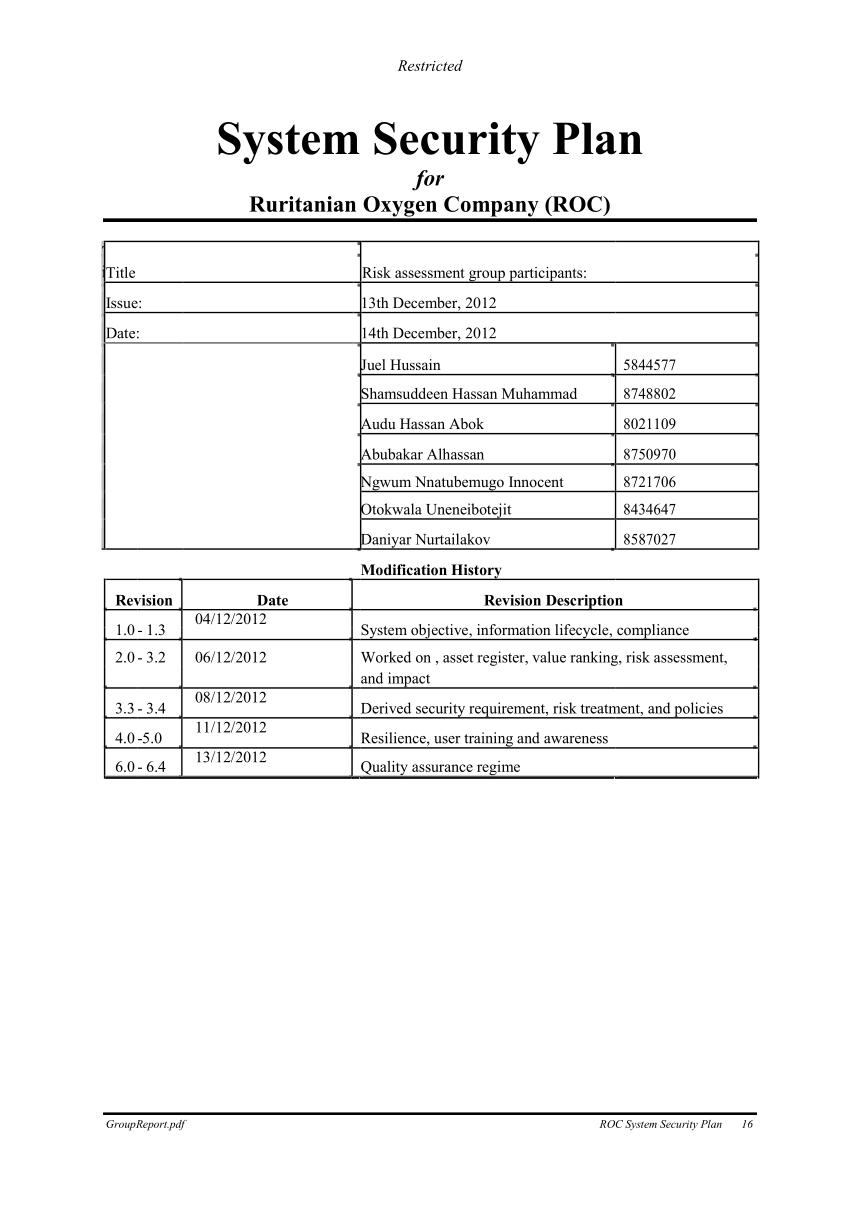
1 System Security Requirements And Describes Controls In Place Or Planned To Meet Those Requirements.
Web Develop, Document, And Periodically Update System Security Plans That Describe System Boundaries, System Environments Of Operation, How Security Requirements Are Implemented, And The Relationships With Or Connections To Other Systems.
Web The Dod's Number One Cybersecurity Requirement Is To Have A System Security Plan.
All Federal Systems Have Some Level Of Sensitivity And Require Protection As Part Of Good Management Practice.
Related Post: