User Access Review Template
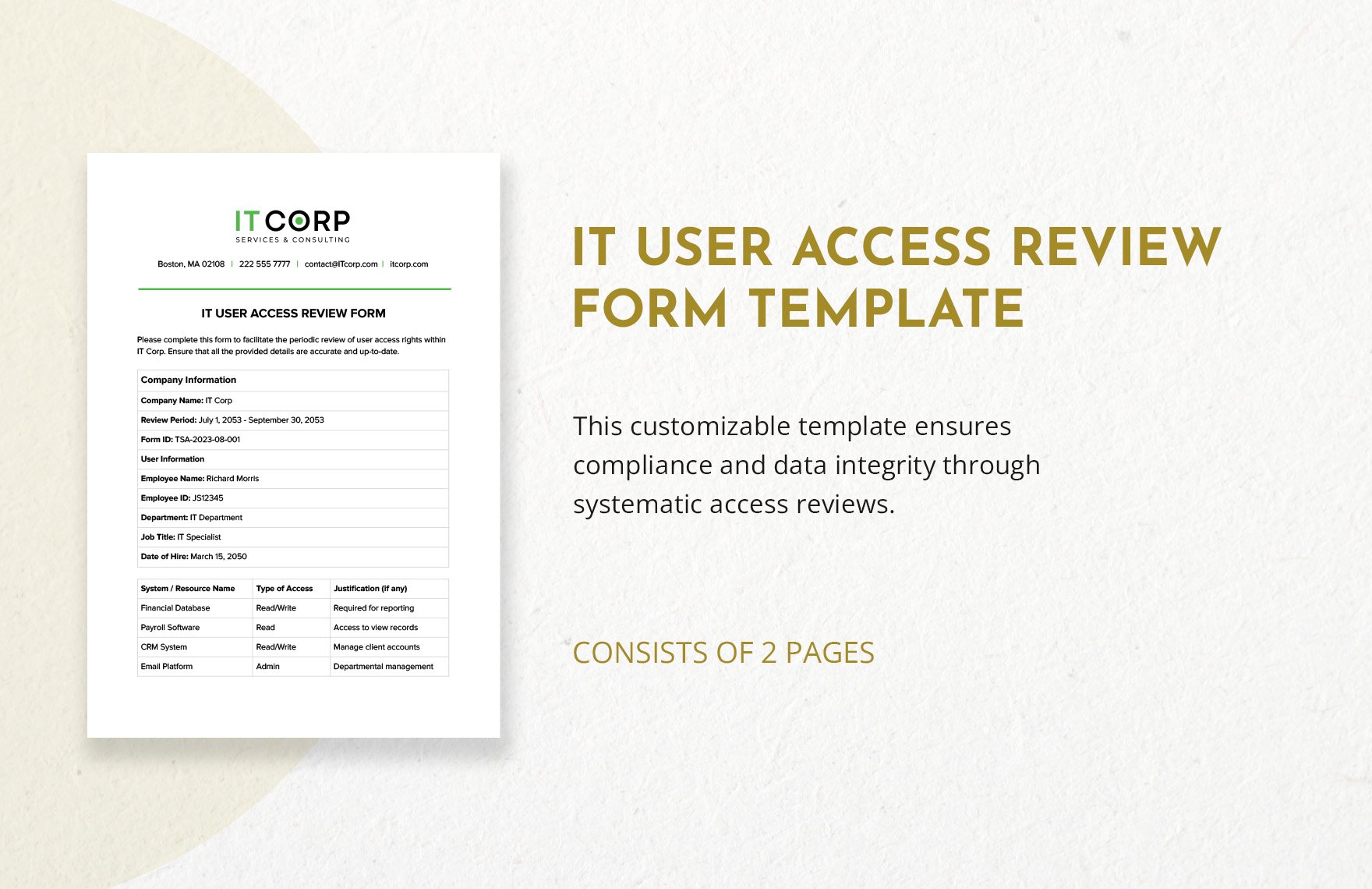
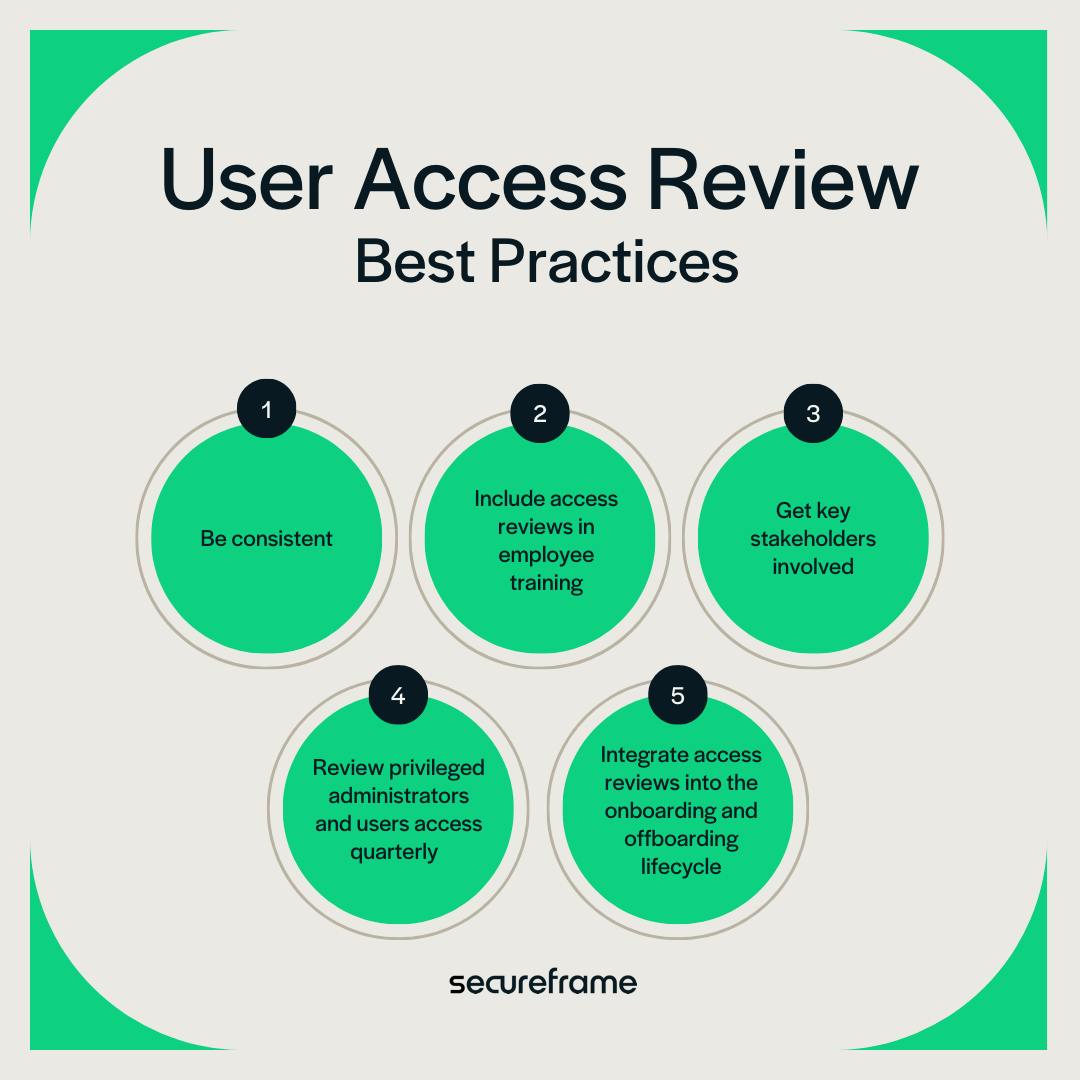
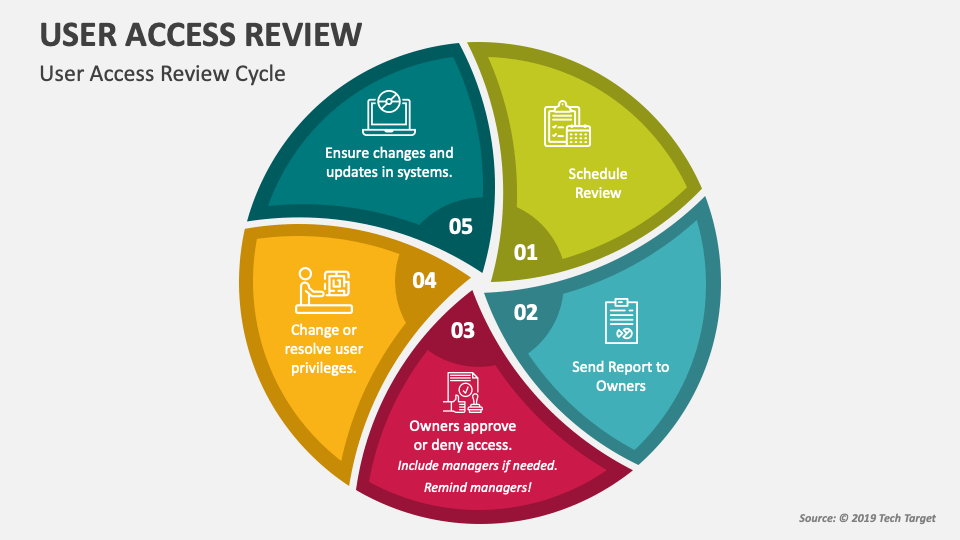
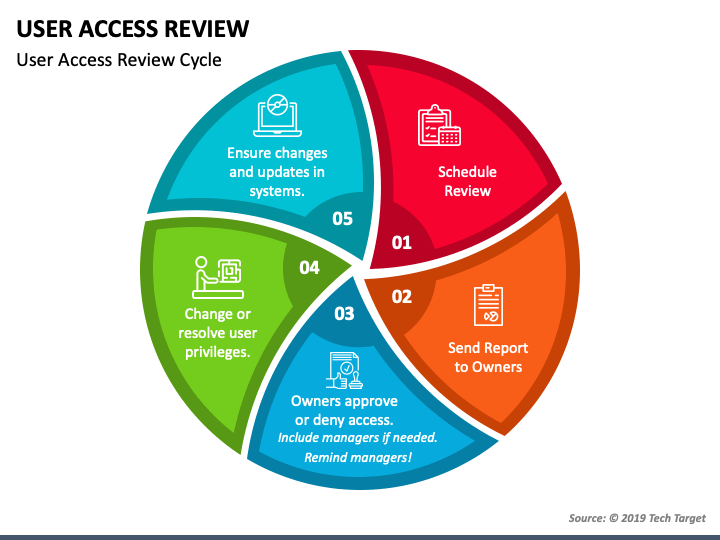
User Access Review Template - An inventory of enterprise assets. To create a user access review policy, gather the following information: Conducting a user access review is necessary for the access management process. Web user access review is a control to periodically verify that only legitimate users have access to applications or infrastructure. Web a user access review template provides it teams with a structured format for quickly conducting reviews. It involves meticulously evaluating user permissions, privileges, and roles within an organization's digital environment. Web user access reviews help identify and address unauthorized or excessive access, reducing the risk of insider threats. In this guide, you will learn everything you need to know about the benefits, challenges and process of user access reviews. This checklist also doubles as documentation for audit purposes. Web by accurately identifying user accounts, you ensure that all relevant accounts are included in the review, avoiding any potential security vulnerabilities and ensuring compliance with access policies. We’ve gathered six best practices for advancing your organization’s user access reviews. Effortlessly evaluate user permissions, align them with roles, and enhance security. Web user access reviews help identify and address unauthorized or excessive access, reducing the risk of insider threats. It involves meticulously evaluating user permissions, privileges, and roles within an organization's digital environment. Web user access review is a control to periodically verify that only legitimate users have access to applications or infrastructure. Web a user access review checklist is designed to guide you through the uar process systematically—guaranteeing that no critical steps are missed and that all aspects of user access and permissions are reviewed. This review ensures that individuals have appropriate access levels to perform their job responsibilities effectively while mitigating the risk of unauthorized access to sensitive information. Use this template to kick off the process. Not all systems require the same level of scrutiny, so it’s important to prioritize based on risk. Web by accurately identifying user accounts, you ensure that all relevant accounts are included in the review, avoiding any potential security vulnerabilities and ensuring compliance with access policies. The template has three tabs: It involves meticulously evaluating user permissions, privileges, and roles within an organization's digital environment. Define the scope of the review. Web a user access review checklist is designed to guide you through the uar process systematically—guaranteeing that no critical steps are missed and that all aspects of user access and permissions are reviewed. This will improve security, reduce unauthorized access risks, ensure regulatory compliance, and maintain efficient access controls. An inventory of enterprise assets. Web a user access review checklist is designed to guide you through the uar process systematically—guaranteeing that no critical steps are missed and that all aspects of user access and permissions are reviewed. Web user access reviews help identify and address unauthorized or excessive access, reducing the risk of insider threats. They help ensure that each user only has the access they need, adhering to the principle of least privilege. Web eliminate the hassle of access reviews mandated by regulations such as sox, hipaa, glba, pci, nydfs, and soc 2. They help ensure that each user only has the access they need, adhering to the principle of least privilege. Use this sheet to track the progress of your review and to sign off each step along the way. This involves determining which systems, applications, and data repositories will be included in the review. Web a user access review template provides. Web a user access review template provides it teams with a structured format for quickly conducting reviews. Web a user access review checklist is designed to guide you through the uar process systematically—guaranteeing that no critical steps are missed and that all aspects of user access and permissions are reviewed. Copy and reuse this worksheet for each system you review.. Simplify access management with our it user access review form template. From creating an access policy and involving stakeholders to embracing the principle of least privilege, here are the essential steps you can take to complete a user access review. Web access reviews are regular audits of user permissions within an organization's software landscape. Copy and reuse this worksheet for. This will improve security, reduce unauthorized access risks, ensure regulatory compliance, and maintain efficient access controls. This checklist also doubles as documentation for audit purposes. Consider using system logs and user directories to gather this information. We’ve gathered six best practices for advancing your organization’s user access reviews. Copy and reuse this worksheet for each system you review. Web by accurately identifying user accounts, you ensure that all relevant accounts are included in the review, avoiding any potential security vulnerabilities and ensuring compliance with access policies. Web user access review is a control to periodically verify that only legitimate users have access to applications or infrastructure. The first step in conducting a user access review is to define. Web by accurately identifying user accounts, you ensure that all relevant accounts are included in the review, avoiding any potential security vulnerabilities and ensuring compliance with access policies. In this guide, you will learn everything you need to know about the benefits, challenges and process of user access reviews. The template has three tabs: Ready to implement user access reviews. To create a user access review policy, gather the following information: Consider using system logs and user directories to gather this information. In this guide, you will learn everything you need to know about the benefits, challenges and process of user access reviews. An example of how to track user access rights and privileges at your organization Web by accurately. This process ensures the right individuals have appropriate access levels based on their job roles and responsibilities. Web easily editable, printable, downloadable. An inventory of enterprise assets. We’ve gathered six best practices for advancing your organization’s user access reviews. Web a user access review template provides it teams with a structured format for quickly conducting reviews. Ready to implement user access reviews at your organization? To create a user access review policy, gather the following information: This process ensures the right individuals have appropriate access levels based on their job roles and responsibilities. They help ensure that each user only has the access they need, adhering to the principle of least privilege. Effortlessly evaluate user permissions,. Copy and reuse this worksheet for each system you review. Effortlessly evaluate user permissions, align them with roles, and enhance security. It involves meticulously evaluating user permissions, privileges, and roles within an organization's digital environment. Web user access review is a control to periodically verify that only legitimate users have access to applications or infrastructure. Web a user access review. Web user access review best practices. We’ve gathered six best practices for advancing your organization’s user access reviews. Web user access review is a control to periodically verify that only legitimate users have access to applications or infrastructure. It involves meticulously evaluating user permissions, privileges, and roles within an organization's digital environment. Web the essential user access review template. This checklist also doubles as documentation for audit purposes. The template has three tabs: Take the following steps, and implement the following best practices to ensure a smooth and effective user access review process. An inventory of enterprise assets. Web a user access review checklist is designed to guide you through the uar process systematically—guaranteeing that no critical steps are missed and that all aspects of user access and permissions are reviewed. Define the scope of the review. This checklist also doubles as documentation for audit purposes. An example of how to track user access rights and privileges at your organization Web eliminate the hassle of access reviews mandated by regulations such as sox, hipaa, glba, pci, nydfs, and soc 2. Use this template to kick off the process. Web easily editable, printable, downloadable.IT User Access Review Form Template in Word, PDF, Google Docs
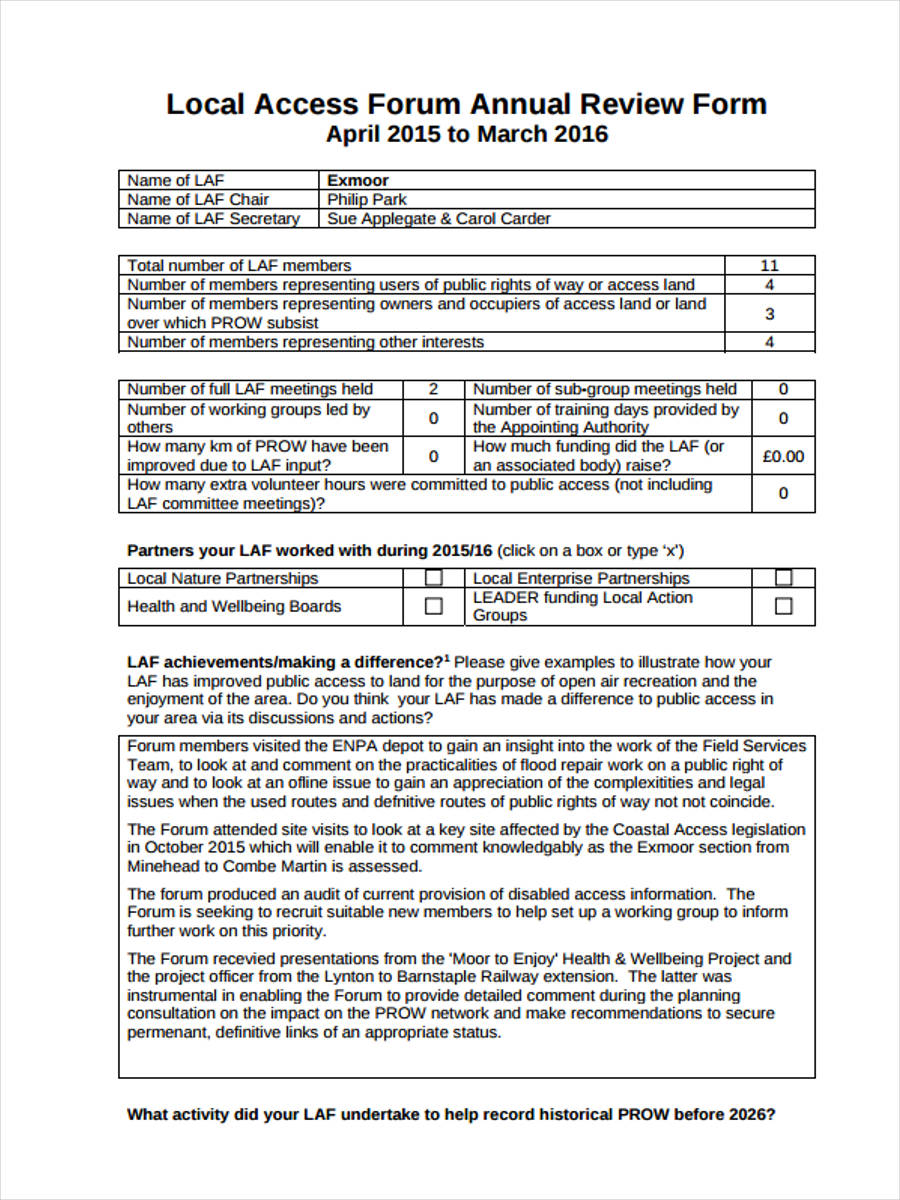
Periodic User Access Review Template
User Access Review PowerPoint Template PPT Slides
User Access Review Template
User Access Review Template
User Access Review Template
A StepbyStep Guide to User Access Reviews + Template
User Access Review PowerPoint and Google Slides Template PPT Slides
The Essential User Access Review Template Rezonate
User Access Review PowerPoint Template PPT Slides
Web User Access Review Template.
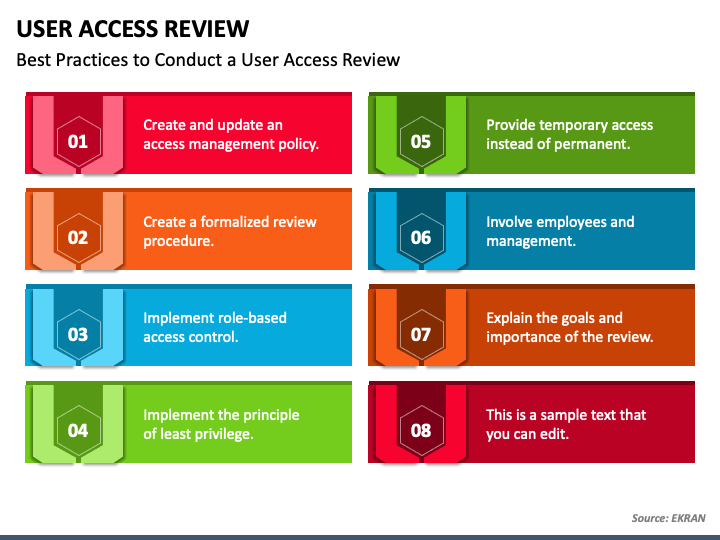
From Creating An Access Policy And Involving Stakeholders To Embracing The Principle Of Least Privilege, Here Are The Essential Steps You Can Take To Complete A User Access Review.
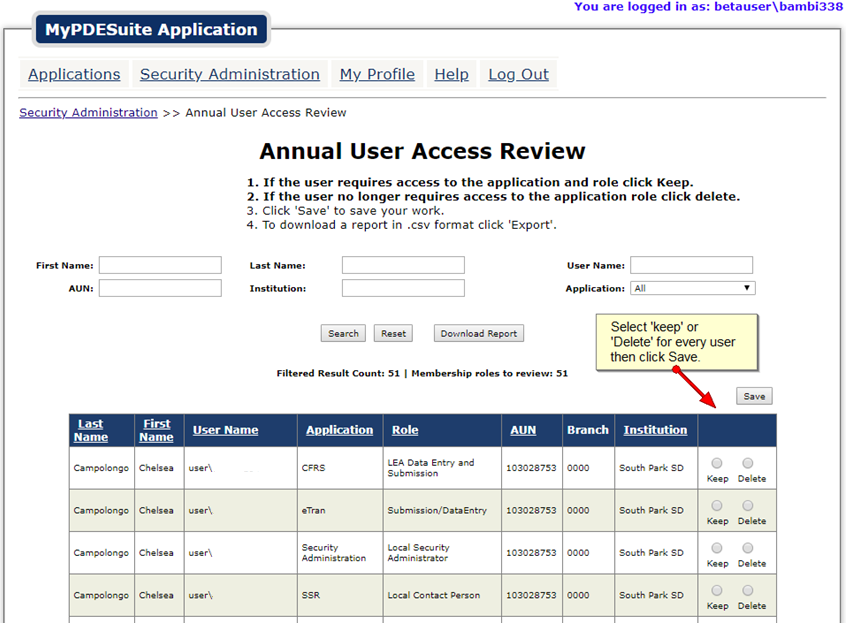
Use This Sheet To Track The Progress Of Your Review And To Sign Off Each Step Along The Way.
Effortlessly Evaluate User Permissions, Align Them With Roles, And Enhance Security.
Related Post: