Vulnerability Report Template
Vulnerability Report Template - Click here to learn more for a. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in addressing said vulnerability during the assessment. Web this guide offers direct access to indispensable cybersecurity risk assessment templates in pdf, word, and google docs formats, enabling organizations. Web vulnerability factors certainly have an effect on whether we fall for scams, but the nature of the scam itself can also impact the likelihood of victimization. Web learn how to create a detailed vulnerability assessment report with this template. Web every vulnerability should follow this template. It is your roadmap to a better state of security preparedness,. Web learn how to write a good vulnerability report for different audiences, including executives, it teams, and regulators. Web sample network vulnerability assessment report. Bug bounty programs ¶ bug bounty programs incentivize. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in addressing said vulnerability during the assessment. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable repeatable functions: Vulnrξpo is a free open source project designed to speed up the creation of it security vulnerability reports and can be used. Web a vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. Bug bounty programs ¶ bug bounty programs incentivize. Web empower your security assessments with sbt's comprehensive vulnerability assessment report template—the roadmap to uncovering, classifying, and mitigating vulnerabilities. Follow the tips on preparing, writing, and formatting your report with examples and references. Web create vulnerability reports like a pro!!! Web vulnerability factors certainly have an effect on whether we fall for scams, but the nature of the scam itself can also impact the likelihood of victimization. It outlines a workflow for identifying, assessing and resolving system and network. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in addressing said vulnerability during the assessment. Web vulnerability factors certainly have an effect on whether we fall for scams, but the nature of the scam itself can also impact the likelihood of victimization. Web a vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. It outlines a workflow for identifying, assessing and resolving system and network. Web tenable vulnerability management provides a selection of report templates and customizable report formats. Web empower your security assessments with sbt's comprehensive vulnerability assessment report template—the roadmap to uncovering, classifying, and mitigating vulnerabilities. A vulnerability report should contain an. Web free threat & vulnerability management templates for organizations to effectively identify and mitigate security risks internally. Web sample network vulnerability assessment report. Follow the tips on preparing, writing, and formatting your report with examples and references. Web (5) a description of how privacy and civil liberties are preserved in the collection, retention, use, and sharing of vulnerability disclosures. Web every vulnerability should follow this template. Bug bounty programs ¶ bug bounty programs incentivize. Web this guide offers direct access to indispensable cybersecurity risk assessment templates in pdf, word, and google docs formats, enabling organizations. Web learn. Web this section is intended to provide guidance for organizations on how to accept and receive vulnerability reports. Web learn how to write a good vulnerability report for different audiences, including executives, it teams, and regulators. Web sample network vulnerability assessment report. Web vulnerability factors certainly have an effect on whether we fall for scams, but the nature of the. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in addressing said vulnerability during the assessment. Web every vulnerability should follow this template. Web learn how to write a good vulnerability report for different audiences, including executives, it teams, and regulators. Bug bounty programs ¶ bug bounty programs. Web (5) a description of how privacy and civil liberties are preserved in the collection, retention, use, and sharing of vulnerability disclosures. Web empower your security assessments with sbt's comprehensive vulnerability assessment report template—the roadmap to uncovering, classifying, and mitigating vulnerabilities. Web this section is intended to provide guidance for organizations on how to accept and receive vulnerability reports. A. Web this section is intended to provide guidance for organizations on how to accept and receive vulnerability reports. Web sample network vulnerability assessment report. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable repeatable functions: Web it is good practice to identify the type of vulnerability you. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to. Click here to learn more for a. Web this guide offers direct access to indispensable cybersecurity risk assessment templates in pdf, word, and google docs formats, enabling organizations. A vulnerability report should contain an. It outlines a workflow for identifying, assessing. Web free threat & vulnerability management templates for organizations to effectively identify and mitigate security risks internally. Web learn how to write a good vulnerability report for different audiences, including executives, it teams, and regulators. Web a vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. A vulnerability is a weakness in an application (frequently a broken. Click here to learn more for a. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable repeatable functions: Web sample network vulnerability assessment report. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to. Web vulnerability factors certainly. Click here to learn more for a. Web learn how to write a good vulnerability report for different audiences, including executives, it teams, and regulators. It is your roadmap to a better state of security preparedness,. A vulnerability report should contain an. Web this section is intended to provide guidance for organizations on how to accept and receive vulnerability reports. Web vulnerability factors certainly have an effect on whether we fall for scams, but the nature of the scam itself can also impact the likelihood of victimization. Web this section is intended to provide guidance for organizations on how to accept and receive vulnerability reports. Web a vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. A. Click here to learn more for a. Web free threat & vulnerability management templates for organizations to effectively identify and mitigate security risks internally. Web (5) a description of how privacy and civil liberties are preserved in the collection, retention, use, and sharing of vulnerability disclosures. A vulnerability report should contain an. Vulnrξpo is a free open source project designed to speed up the creation of it security vulnerability reports and can be used. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in addressing said vulnerability during the assessment. Web vulnerability factors certainly have an effect on whether we fall for scams, but the nature of the scam itself can also impact the likelihood of victimization. It outlines a workflow for identifying, assessing and resolving system and network. Bug bounty programs ¶ bug bounty programs incentivize. Web learn how to create a detailed vulnerability assessment report with this template. Follow the tips on preparing, writing, and formatting your report with examples and references. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to. Web every vulnerability should follow this template. Web a vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. Web empower your security assessments with sbt's comprehensive vulnerability assessment report template—the roadmap to uncovering, classifying, and mitigating vulnerabilities. Web create vulnerability reports like a pro!!!Free Sample Vulnerability Assessment Report PurpleSec
Vulnerability Reporting Template
Vulnerability Assessment Template Download Printable PDF Templateroller
Vulnerability Report Template
Vulnerability Assessment Report Template Fill Out, Sign Online and
Vulnerability Scan Report Template
Vulnerability Management Report Template
Critical and Exploitable Vulnerabilities Report SC Report Template
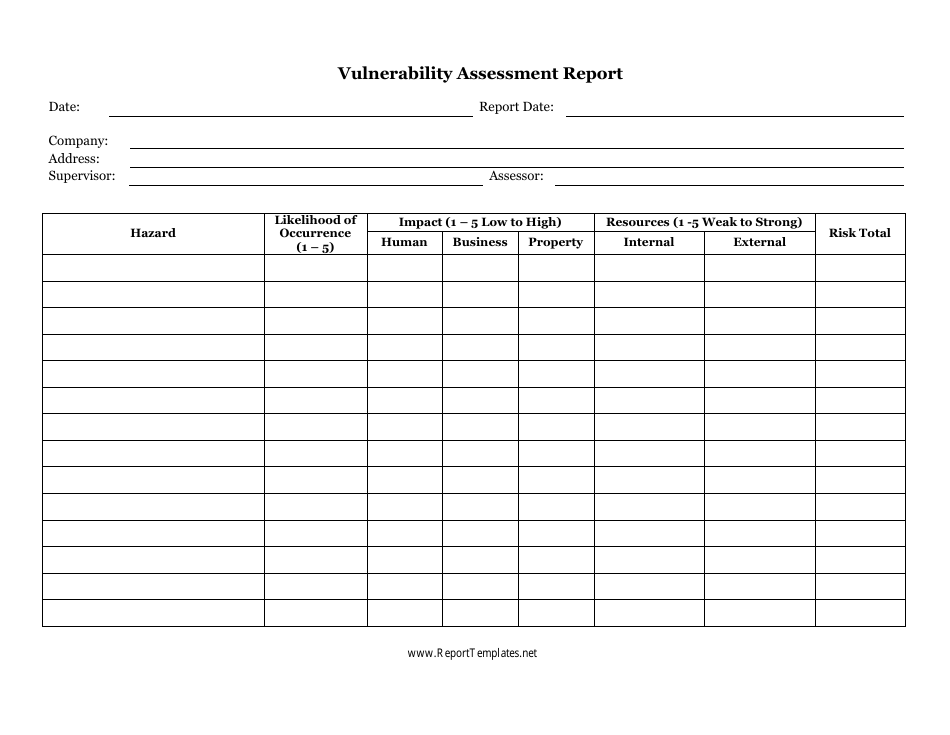
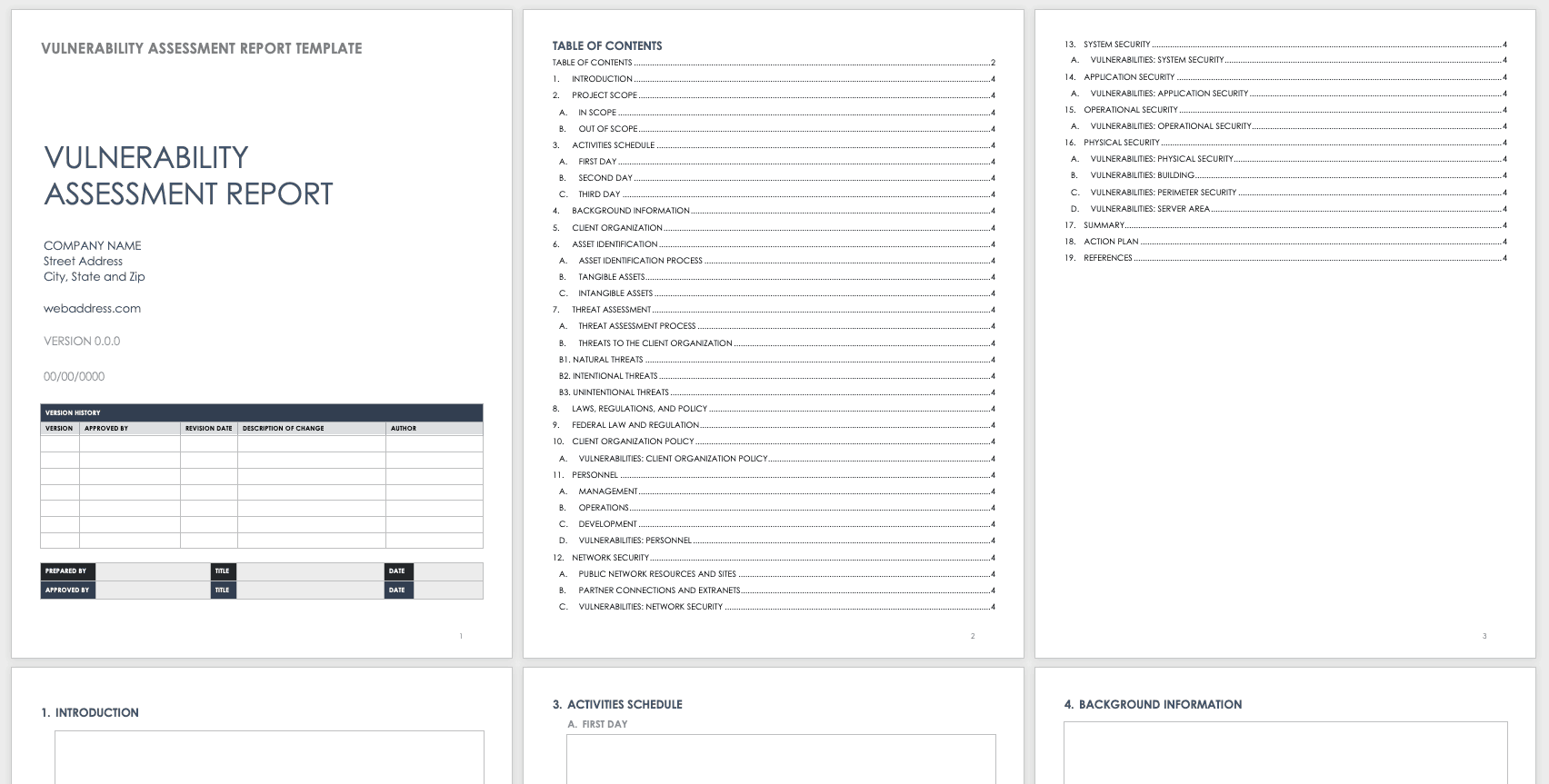
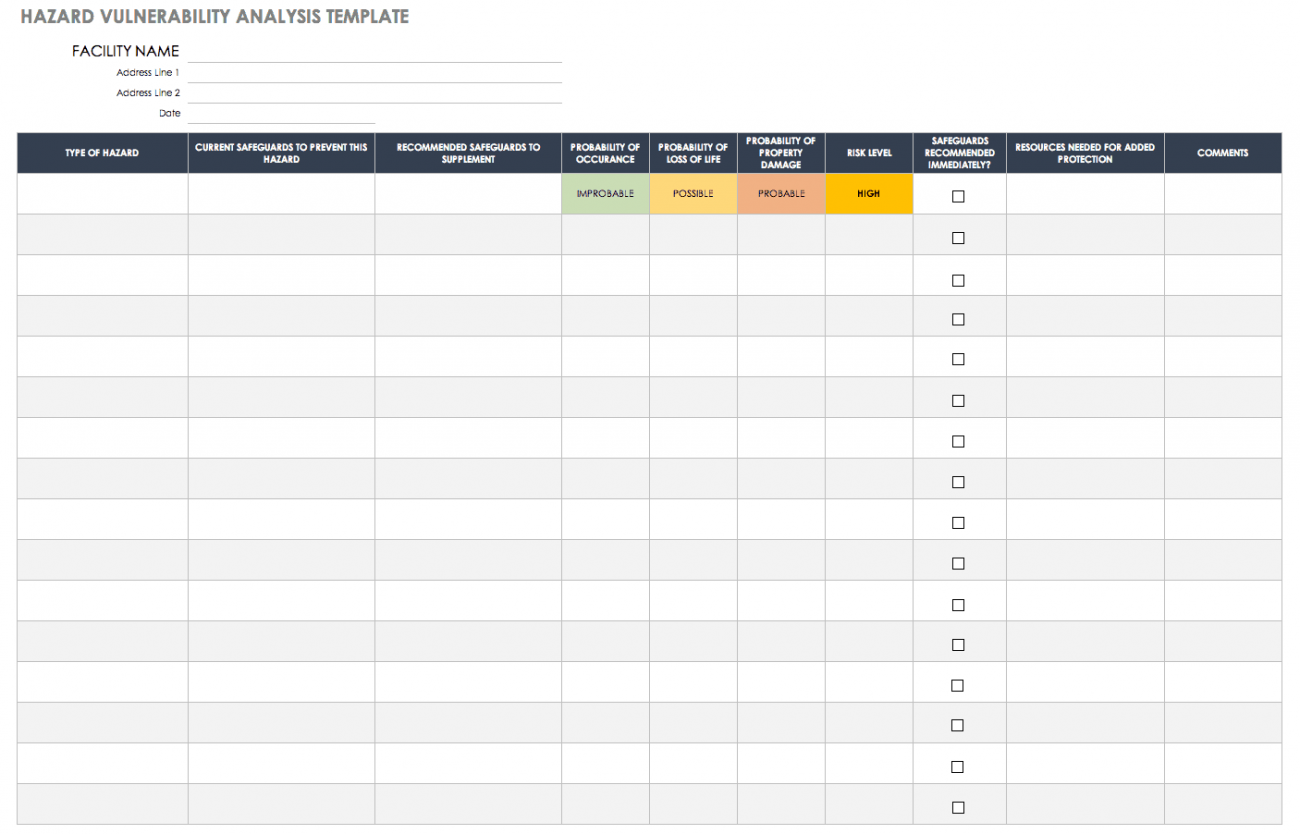
Free Vulnerability Assessment Templates Smartsheet
Free Vulnerability Assessment Templates Smartsheet
Web Learn How To Write A Good Vulnerability Report For Different Audiences, Including Executives, It Teams, And Regulators.
Web This Guide Offers Direct Access To Indispensable Cybersecurity Risk Assessment Templates In Pdf, Word, And Google Docs Formats, Enabling Organizations.
It Is Your Roadmap To A Better State Of Security Preparedness,.
Web This Section Is Intended To Provide Guidance For Organizations On How To Accept And Receive Vulnerability Reports.
Related Post: